After migrating everything (we thought) to our new Domain controllers, we decided to disable the network card of our last old Domain controller. After doing this we had some strange errors in the cluster events and cluster logging. So we decided to enable our network card back again. In this blog I will take you to the troubleshooting steps we have taken to determine the root case.
The issue:
Errors in the cluster events:
Cluster resource ‘Cluster Name’ of type ‘Network Name’ in clustered role ‘Cluster Group’ failed.
Based on the failure policies for the resource and role, the cluster service may try to bring the resource online on this node or move the group to another node of the cluster and then restart it. Check the resource and group state using Failover Cluster Manager or the Get-ClusterResource Windows PowerShell cmdlet.
Errors in the cluster log:
INFO [RES] Network Name: [NNLIB] Bind to last known DC \WRONGDC failed with error 1722. Finding a new suitable DC
INFO [RES] Network Name: [NNLIB] FindSuitableDCNew – objectName CL2-###-###, username – CL2-###-###$, firstChoiceDCName –
INFO [RES] Network Name: [NNLIB] LDAP bind to first choice DC failed. Error 1326. Trying second choice DC
INFO [RES] Network Name: [NNLIB] LDAP bind to second choice DC failed. Error 1326.
ERR [RES] Network Name: [NNLIB] Finding suitable new DC failed with error 1326.
WARN [RES] Network Name : AccountAD: PopulateSuitableDCExisting – FindSuitableDCExisting failed with error 1326 with known good password. Retrying with proposed password
INFO [RES] Network Name: [NNLIB] Bind to last known DC \WRONGDC failed with error 1722. Finding a new suitable DC
INFO [RES] Network Name: [NNLIB] FindSuitableDCNew – objectName CL2-###-###, username – CL2-###-###$, firstChoiceDCName –
INFO [RES] Network Name: [NNLIB] LDAP bind to first choice DC failed. Error 1326. Trying second choice DC
INFO [RES] Network Name: [NNLIB] LDAP bind to second choice DC failed. Error 1326.
ERR [RES] Network Name: [NNLIB] Finding suitable new DC failed with error 1326.
ERR [RES] Network Name : AccountAD: PopulateSuitableDCExisting – FindSuitableDCExisting failed with error 1326 with known proposed password
ERR [RES] Network Name : AccountAD: PopulateNetnameADState – Populate suitable DC existing failed with error 1326
ERR [RES] Network Name : AccountAD: Populate netname AD state (bind to DC & search for existing object) for object CL2-###-### failed with error 1326
INFO [RES] Network Name : AccountAD: OnInitializeEnd: 1326
INFO [RES] Network Name: Agent: OnInitializeReply, Failure on (fff119da-8df0-4eae-872e-9f38a9805479,AccountAD): 1326
INFO [RES] Network Name : Configuration: AccountADInitReplyHandler – Received result 1326 from AccountAD
Troubleshooting steps and the solution
- Lets check if we can find any connections to our old system with netstat. So we run the query:
|
1 |
Netstat -a -p tcp | findstr OLD_DC |
- And yes, there it is. A LDAP connection from our cluster node who owns the Cluster IP.
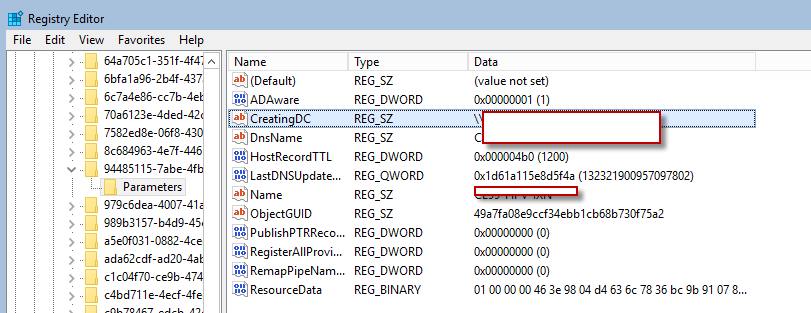
- Check we can find something in the Windows Register about that old DC. So we opened regedit and searched for the old DC Name.
- Again we found our old DC in some guid directory like this picture.
- Next, check if we can find something in our cluster parameters giving the same:
|
1 |
get-ClusterResource | ?{$_.ResourceType -EQ "Network Name"} | Get-clusterparameter dnsname,creatingdc,RegisterAllProvidersIP |ft ClusterObject,Name,Value |
- Maby we could change that one with Set-clusterpameter.No luck because the property is read-only.
- After reading more about the cluster name resource we know that we can do some repairing actions without affecting anything.
- So we bring the “cluster name resource” offline. And click repair action.
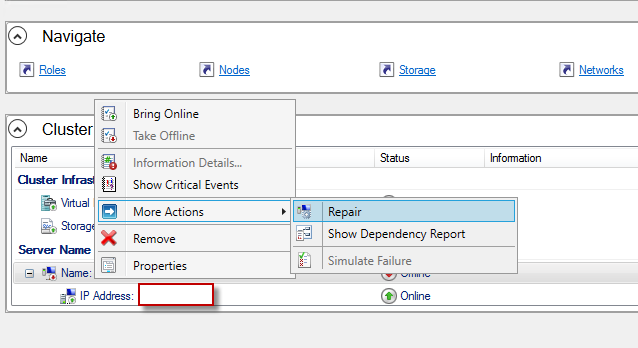
- After some minutes the cluster name resource became online. But still no luck.
- The final solution for us was: Moving the cluster computer object to a OU with more rights (in our situation was the default Computers OU) suitable.
- After the move, repeat step 8 (repair) and wait some minutes till everything is replicated. Everything was fine again 🙂
- Now we could safe demote our old Domain Controller.